Organizations Lack Basic Security Hygiene
The number of hacking attempts on companies is constantly rising. Many of them result in data being exfiltrated or encrypted and held for ransom (ransomware attacks). Analysis of these attacks shows that most of them would be prevented by simple security hygiene within a company’s environment. Microsoft’s 2023 Digital Defense Report shows that an estimated 99% of attacks are preventable with basic security hygiene.
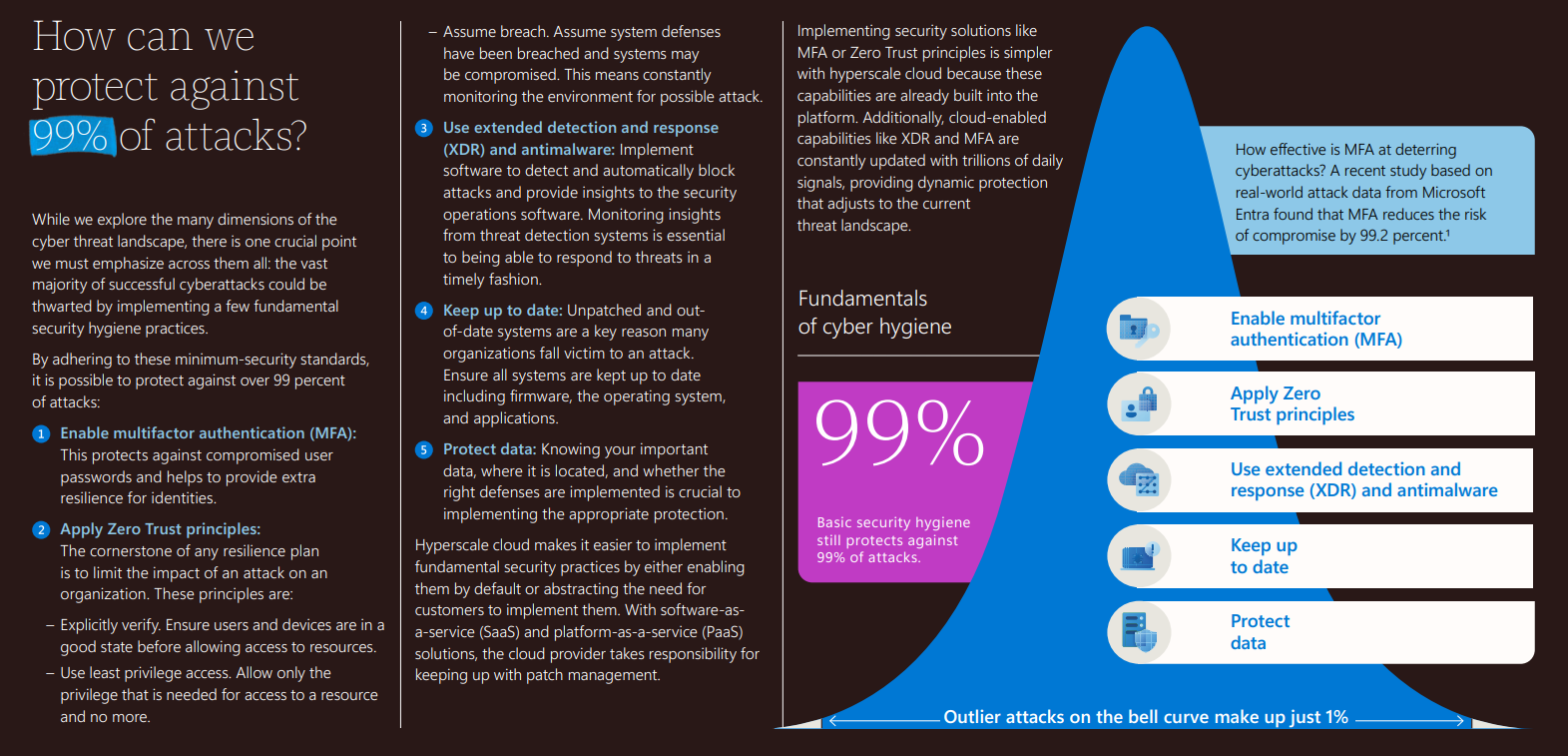
Source: Microsoft Digital Defense Report
Unfortunately, several companies are not actively engaging in their basic security hygiene due to a perceived lack of ROI and a focus on maximizing short-term profits. This means that these corporations are vulnerable and are not actively acknowledging their vulnerability to themselves. This could result from a lack of engagement in penetration testing, failure to continuously review the security of their digital environment, or simply a lack of prioritization given the staffing levels within a corporation. With the expansion of AI tools over the past year, the number of attacks has and will continue to rise, and once a breach occurs, the necessary response time is decreasing.
Protection Strategies
Protecting a company in today’s environment requires a full defense-in-depth strategy, utilizing tactical utilization of both defense in layers and zero trust, focusing on zones or areas covering the entire company. These zones boil down to ingress prevention, activity within the company environment, and egress from the environment. The solutions can cross zones and focus on preventing access, knowing what is going on within the company to identify any unusual behavior or activity, and ensuring that any data leaving the company is either known or of no value after it leaves the environment.
1. Preventing Unauthorized Access
The first item is to prevent unauthorized access to the environment. This means verifying that the user is who they say they are, ensuring the device they are connecting from is secured, and that the risk level between the user, device, and location is not putting the company in jeopardy. Separating elevated rights accounts from everyday accounts and limiting access based on account, device, and location are recommended. It should be noted that this applies not only to users but also to applications and services that fall under what is being tracked and limited. The goal is to have a set of conditions for every layer within a company and ensure ongoing verification before allowing access.
2. Monitoring the Environment
The second item is to focus on monitoring what is happening within the environment, which aligns with the principles of zero trust. Starting by establishing a baseline of day-to-day, quarterly, and yearly activities is crucial for identifying deviations from normal behavior. This can be easily monitored with an environmental integration of services into a single solution. Ensuring that all activity is monitored, setting and regularly reassessing alerts, and curating the types of applications in use to protect against unauthorized software is essential. Identity protection includes limiting the time an elevated account can be used (Just in Time access), requiring elevated accounts to go through an approval process, separating accounts (everyday accounts vs. administrative accounts), and applying the principle of least permissions required. Protecting services by breaking apart the network into micro-segments provides an additional layer of defense. Integrating endpoint defenses to align with cloud policies helps ensure they are protected before granting access. Labeling all data as it is created through client labeling policies and adding policies on the service side to examine and label data when it enters from outside of the company are vital steps.
3. Data Egress Management
The third item is to protect when data egresses from the environment. Enforcing encryption for sensitive data that requires the reader to be logged into the environment is key. It is also important to ensure that data that is exposed, shared, or collaborated on has a limited lifespan for offline viewing or any viewing once outside of the environment. Including data loss prevention policies to cover every aspect of data egress and considering what can reach out of the environment when dealing with IoT devices and appliances are key measures.
In summary, with the increase in attacks on companies across the globe, it is essential to evaluate the fundamentals of security throughout a company’s environment for potential vulnerabilities. At Valorem Reply, this is something that we do with our Security Assesment process by focusing on the overall health of the company based on strategic goals and then breaking it down into tactical activities that will close the identified gaps. This is a necessary step that should not be overshadowed by ongoing discussions about AI. The worst thing a company can do is chase the AI brass ring, only to lose because they haven’t ensured that the basics of their security foundation are secure.
